Knowledge Management for Standard Chartered PLC
Knowledge management entails organisation sharing their expertise and resources, and building intellectual capital to boost competitiveness. Organisations with intranets embrace knowledge management to enable employees to learn different advances in technology and acquire information and expertise in the corporation. Corporations also bank on knowledge management to capture knowledge and practice before experts leave the company through retirement or for whatsoever reason, to avoid losing valuable information build through several years of hard work (Moffett and Walker, 2015, p 102). However, maintaining security is cited as the most threatening challenge in knowledge management. Knowledge management encompasses numerous technologies including multimedia collaboration, data mining and the web. As such, security in the multimedia collaboration systems and web data management all factor in when it comes to security knowledge management systems and practices. Besides, there is a need to protect the organisation’s assets, including intellectual property. The corporation’s trade secrets must be kept confidential to prevent access by competitors. The organisation must therefore enforce various access control forms, including encryption, role-based access and credential management to protect valuable data (Fullwood and Rowley, 2017, p 63). Therefore, the present paper explores the approaches to securing knowledge safety for Standard Chartered PLC, alongside suggesting possible changes that can be adopted to improve knowledge safety, cybersecurity, and protection of intellectual property rights held within the organisation.
Existing Approaches to Securing Knowledge Safety within Standard Chartered PLC
This section explores the existing approaches and technologies adopted by Standard Chartered PLC to manage cybersecurity and related threats to the organisation’s knowledge safety. Cybersecurity remains Standard Chartered Bank’s top priority even as the firm strengthen its digitisation efforts following the aftermaths of Covid-19 pandemic according to the company’s cybersecurity executive (Standard Chartered 2020). The company is prone to cybersecurity threats due to the nature of its business. Research shows that financial and banking institutions are 300 times prone to cyber-attack than other firms. Cybersecurity threats invite a significant financial loss to the banks as they have to prevent or manage the cyber-attacks and upshot effects (Johnson, 2016, p 277). Common cybersecurity threats for the financial institutions include credential and identity theft, data manipulation and theft, disruptive and destructive malware threats, advance cyber-threats from emerging technologies such as 5G network, and misinformation. Most of the attacks are executed through denial-of-service (DDoS), malware, and phishing attacks (Johnson, 2016, p 278). However, several approaches and technologies discussed below are adopted by Standard Chartered PLC to manoeuvre such cybersecurity threats.
Safety Tech
According to the company website report, Standard Chartered relies significantly on Safety Tech to block access to “dark net” platforms and malicious websites. “By working with safety tech, we can now better understand the criminality of the networks that we are dealing with, and how we can get under their skin and put up defences to prevent abuse of our systems and our clients,” said Patricia Sullivan, the company’s Managing Director for Financial Crime Compliance (Standard Chartered 2020). Safety Tech is a term applied in the business world to refer to a wide range of technology ranging from safety software to wearable and is increasingly becoming a popular method of reducing risk and associated costs. By understanding SafetyTech, Standard Chartered can better respond to ransomware threats and offer more digital and safer banking. Safety Tech primarily aims to ensure that human is safe and resilient when interacting with technology (More and Nalawade, 2015, p 12).
Standard Chartered Bank emphasises on training the employees on Safety Tech to increase their cyber-situational consciousness; hence becoming more conscious of their “digital exhaust,” defined as the detectable traces that individuals leave on the internet platforms such as social media. Standard Chartered pride itself as the first financial and banking organisation to recognise the significance of Safety Tech from both a “financial crime compliance (FCC)” standpoint and as an approach to “creating long-term resilience.” Safety Tech expresses the company’s three “Sustainable Agenda Pillars,” including “Responsible Company, Sustainable Finance and Inclusive Communities.” By making certain that people are just as secure from cybersecurity attacks as are data and machines, Standard Chartered Bank promotes the sustainable inclusion of their customers while at the same time protecting their workforces from cyber-attacks related harms (Standard Chartered 2020). Standard Chartered Bank, just like other financial institutions, also uses antiviral, firewall and anti-malware application and vulnerability scanning to detect and manage intrusions.
Authentication Tools
The bank also relies on authentication tools to ensure that individuals accessing information are certainly whom they present themselves to be and are the account’s rightful owner in question. Authentication process helps to identify someone based on one or a combination of three facets: “something you have, something you know or something you are.” For instance, the commonly adopted authentication is the user ID and password. But this mode of authentication is easily compromised, and stronger authentication is sometimes necessary. For instance, identifying customers with what they are, including their physical characteristics such as fingerprint or eye-scan, is difficult to compromise (Xu and Wu 2015, p 10). This mode of authentication used by the bank is called biometric user identification. The most secure authentication method embraces a multi-factor approach that combines more than one factor, making it difficult for someone to falsify themselves.
Access Control
The bank also uses access control to establish the users authorised to access, read, modify/alter, add or delete information. Once the user is validated, it is imperative to ensure that they can access correct information resources, which is achievable through access control. Standard Chartered Bank uses two access control models: role-based access control (RBAC) and access control list (ACL). ACL approach entails creating a list for users who can take designated actions within an information system, such as write, read or modify (add or delete). Users not listed in the ACL may not even know that an information resource is present. However, researchers argue that ACL has several drawbacks (Bourgeois and Bourgeois, 2014, p 74). The most cited challenge is that every information resource in the ACL is managed independently, making it challenging for security administrators to remove a user to an expansive set of information resources. ACLs are challenging to maintain when the users increase, which provides leeway for cybersecurity attackers to penetrate the system unnoticed (Bourgeois and Bourgeois, 2014, p 76). Such difficulties have led to an improved approach to access control, referred to as role-based access control (RBAC) to complement the ACLs.
RBAC does not give users direct access to an information resource. Instead, the users are assigned roles, and the roles are assigned access. The mode of operation enables information system administrators to manage roles and users separately, simplifying system administration responsibilities, and by extension, enhancing security knowledge safety (Bourgeois and Bourgeois, 2014, p 78). Figure 1 below is a comparison between ACL and RBAC as used by Standard Chartered Bank.
Figure 1: ACL and RBAC
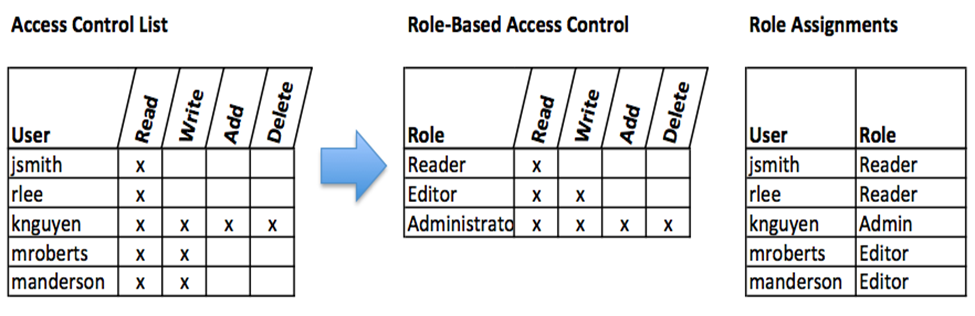
Source: (Bourgeois and Bourgeois, 2014).

ORDER A CUSTOM ESSAY NOW
HIRE ESSAY TYPERS AND ENJOT EXCELLENT GRADES
Encryption
Often, firms transfer information to external media, including flash drive and CDs or transmit the same over the internet. In such scenarios, even with sophisticated access control and authentication, the data can be accessed by an authorised person. Standard Chartered Bank, just like other large organisations, uses encryption to prevent unauthorised data information access. Encryption technology encodes data upon transmission and storage so that only authorised persons can read it. The encoding is done by a computer program, which encrypts plain text being transmitted, and the receiver receives the ciphertext, which is decoded through the decryption process (Lozupone, 2018, p 42). Encryption is essential for financial and banking institutions to prevent third parties from accessing sensitive data such as password and account details sent to customers through electronic media (Lozupone, 2018, p 43). The encoding and decoding of information between the bank and the customers take the form of asymmetric encryption. In asymmetric encryption, two keys are adopted: private and public key. In this case, sending an encrypted message involved obtaining the public key, encoding the message and sending it. The receiver then applies a private key to decode the message. A private key is essential to decrypt a text sent with a public key (Lozupone, 2018, p 44). Figure 2 shows an asymmetric/public key encryption adopted by the bank.
Figure 2: Asymmetric/Public Encryption

Source: (Lozupone, 2018).
Backups
Another important security knowledge safety adopted by the bank is a comprehensive backup plan for the whole organisation to prevent loss of sensitive data in cybersecurity attacks. The organisation backs up the data on the corporate’s server and every computer used within the company (Bourgeois and Bourgeois, 2014, p 37). Information is a strategic asset for Standard Chartered, just like other banking and financial institutions. The entire industry has sprung up around technologies essential to implement a robust backup strategy.
Firewalls
Another method that the bank uses to enhance the security of its information system is the firewall. Standard Chartered bank uses both hardware and software firewalls. The hardware firewalls are connected directly to the network purposefully to filter the packets according to set rules. On the one hand, the software firewalls run on the operating systems and interrupt packets as they arrive on the company’s computer systems. Firewalls protect all the company computers and servers by stopping any packet from outside the bank’s network that does meet the stringent set criteria (Möckel and Abdallah, 2010, p 153). The firewalls can also be configured to restrict packets that leave the organisation. This is done to prevent the possibility of workers accessing sites from Facebook or other platforms that may contain malicious links (Möckel and Abdallah, 2010, p 149). Figure 2 is an example of firewall configuration for the Standard Chartered E-banking.
Figure 1: Network Configuration with Firewalls for E-Banking
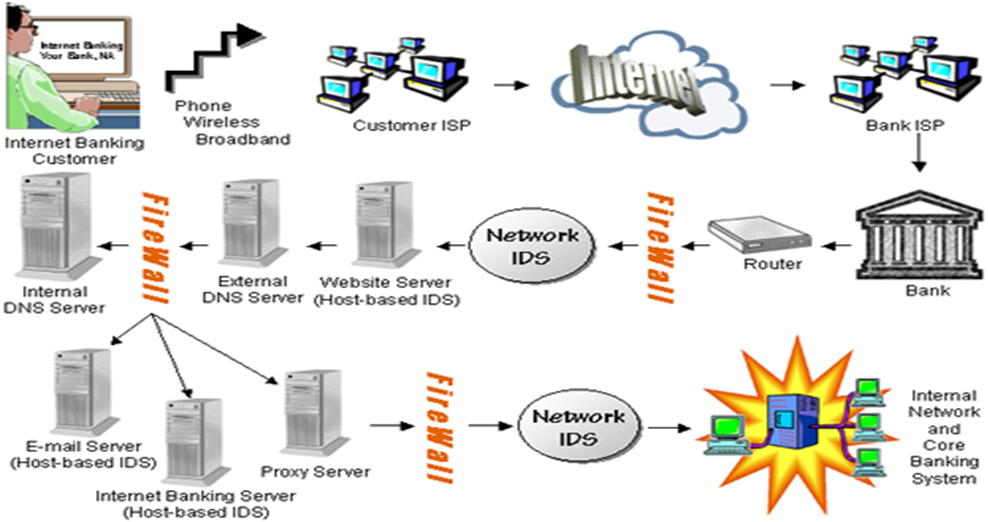
Source: (Möckel and Abdallah, 2010).
Possible Changes to Improve Organization’s Knowledge Safety, Cybersecurity and The Protection of Intellectual Property
Even though Standard Chartered Bank adopts several robust approaches and technologies to prevent cybersecurity attacks on the company’s information system and protect its intellectual property, there still gaps that need to be filled to match and defend against the ever-evolving cyber threats. Security teams in the financial and banking sectors are experiencing even more advanced and challenging demands as they defend their companies in an environment characterised by new and unexpected cybersecurity threats. Many modifications can still be implemented to the firm’s secure knowledge management that goes beyond the commonly adopted approaches and technologies. The following areas can be modified to ensure more security for the company’s information system.
Secure Knowledge Management Architecture
As mentioned earlier, secure knowledge management encompasses secure processes, strategies and metrics necessary to protect the organisation’s information system and intellectual property. An overhaul in the company’s knowledge management system is essential to incorporate additional elements such as strategic protection and emerging technologies to ensure robust knowledge management. This can be accompanied by modification of the existing secure knowledge safety systems such as a firewall. For instance, the company’s security processes and procedures for knowledge management should incorporate an integrated secure workflow process for order management, contracting and purchasing.
Security must be incorporated into any of the company’s processes for contracting, workflow, order management and purchasing, ensuring that only designated users with particular credentials can conduct various knowledge management functions. The company’s metrics for secure knowledge management and control should primarily emphasise the influence of security on the organisation’s knowledge management metrics. For instances, knowledge-management metrics may encompass the number of a patent obtained and volumes of documents published. When security is integrated into the workflow processes, the volume of documents published may decline as some documents become classified (Hota, Upadhyaya and Al-Karaki, 2015, p 986). Random experiments are necessary to establish the impact of security on various metrics sampled.
Unified Connectivity (UCON)
The organisation can also adopt unified connectivity (UCON) technology for knowledge management alongside other forms discussed earlier to enhance information system security further. The concept of unified connectivity (UCON) was lately introduced in the information technology security literature in an attempt by researchers to extend access control metrics and models beyond the basic matrix of Lampson, which dominated the field of secure knowledge management for close to three decades. The idea of unified connectivity connects different extensions of secure knowledge management, such as digital rights and trust management. The UCON model provides an expansive information system security framework for “next-generation access control.” The model comprises of six components: objects and associated attributes, subject and their attributes, authorisation, rights, conditions and obligations (Hota, Upadhyaya and Al-Karaki, 2015, p 983). The obligations, authorisations and conditions are the decision components of the UCON model. The authorisation rules either permit or deny subjects’ access to objects with specific rights based on the object or subject attributes, including security classification, role names, credit amount or clearance. The attributes are considered variables with specific values assigned to them in every system state (Hota, Upadhyaya and Al-Karaki, 2015, p 984).
The unified connectivity model is an attribute-based matrix where permission is authorised based on the object’s value and subject attributes. The model extends beyond the conventional access control matrix in that the control decision relies on both obligations and conditions, as opposed to obligations only. Obligations refer to a series of activities completed by an object or the system such keying in the user name and password to sign in to a website. On the one hand, conditions are environmental restrictions and systems that are not necessarily linked to object or subject attribute; hence creates patterns not easy to predict by an intruder. Another aspect that differentiates UCON from the traditional access control matrix is the aspect of mutability and continuity. Continuity implies that a complete UCON process comprises of three phases: “along the time—before usage, ongoing usage, and after usage.” The control-decision facets are crosschecked and imposed in the first two phases called the pre-decision and ongoing-decisions (Hota, Upadhyaya and Al-Karaki, 2015, p 985).
On the one hand, mutability implies he ability to update the object and subject attributes to new values during access. The updates alongside operations of the three phases are executed and monitored by the installed security system to access the subject to object. UCON’s mutability and continuity make the model very powerful for information system security (Hota, Upadhyaya and Al-Karaki, 2015, p 984). The UCON’s emerging power is very relevant to the computerised and seamless information security management in the financial and banking environments and is essential for Standard Chartered Bank in ensuring the security of both local and global information systems. Figure 3 illustrate the core of UCON model.
Figure 3: UCON model
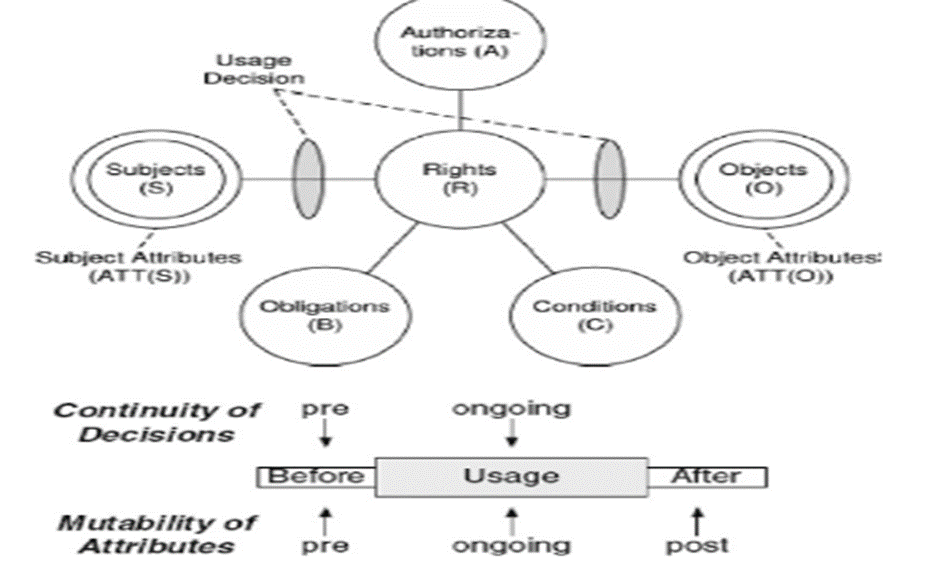
Source: (Hota, Upadhyaya and Al-Karaki, 2015).

- FAST HOMEWORK HELP
- HELP FROM TOP TUTORS
- ZERO PLAGIARISM
- NO AI USED
- SECURE PAYMENT SYSTEM
- PRIVACY GUARANTEED
Intellectual Property Management System (IPMS)
The Standard Chartered should also adopt a comprehensive and integrated IPMS system, an administrative and policy tool that helps accumulate and further guarantee the value of a rich intellectual property portfolio. The company’s intellectual property implementation should involve the contribution from different firm subsystems, which helps define the organisation’s intellectual property management portfolio (Kim and Kim, 2018, p 2600). A comprehensive intellectual portfolio management system for the company should have five fundamental areas of responsibility: 1) generation of intellectual property (IP); 2) IP portfolio management; 3) IP valuation; 4) competitive assessment; 5) Strategic decision-making. Having a comprehensive IPMS is essential in maintaining the complete inventory of the company’s IP, establishing the IP asset value, estimating the expected revenue and the contribution of the IP to the organisation’s profitability and protecting the organisation’s intellectual property rights (Holgersson and Aaboen, 2019, p 126).
Conclusion
This essay explores the various approaches to securing knowledge management adopted by Standard Chartered PLC, and possible modifications and new technologies that the company adopt to improve knowledge safety, cybersecurity and protection of intellectual property rights held within the organisation. The company currently uses different approaches to securing knowledge safety, such as Safety Tech, and various other information system security management technologies such as access control, authentication technologies, and firewall and encryption systems. However, the researcher has identified different mechanisms and technologies that can be integrated into the current system to enhance information resources security. Such include integrating secure workflow processes for order management, contracting and purchasing, UCON and robust IPMS.
Bibliography
Bourgeois, D. and Bourgeois, D.T., 2014. Information Systems Development. Information Systems for Business and Beyond.
Fullwood, R. and Rowley, J., 2017. An investigation of factors affecting knowledge sharing amongst UK academics. Journal of Knowledge Management.
Holgersson, M. and Aaboen, L., 2019. A literature review of intellectual property management in technology transfer offices: From appropriation to utilisation. Technology in Society, 59, p.101-132.

